why
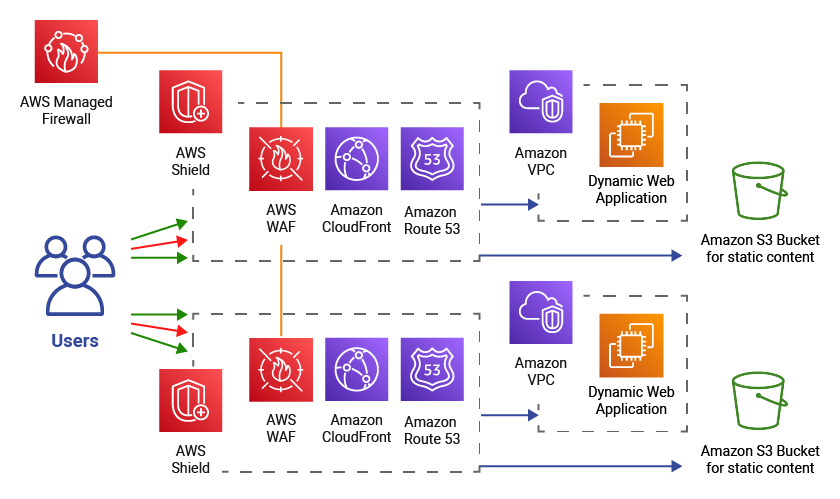
Running public websites, i.e. e-commerce platforms, IoT applications and portals, always require public access from all over the internet. To protect those dynamic web applications against external attackers as good as possible, you need to implement a so called perimeter protection.
With Perimeter protection, you establish a resilient multi-layer security strategy and protect your applications from bugs and vulnerabilities, even zero-day-attacks. Additionally, you protect your applications against multiple types of Distributed Denial of Service (DDoS) attacks.
what
Alice&Bob.Company provides perimeter protection as a managed service. The goal is to secure customers’ applications and origin infrastructure from cyber security attacks such as Distributed Denial of Service attacks, SQL Injection or Cross-Site Scripting.
This suite of services includes
- AWS Managed Firewall,
- AWS WAF,
- AWS Shield, and
- AWS Firewall Manager
Alice&Bob.Company is directly connected with the AWS DDoS Response Team (DRT). This means, in case of a cyber-attack affecting your infrastructure, A&B is quickly able to escalate within the organization, within known processes and structures.
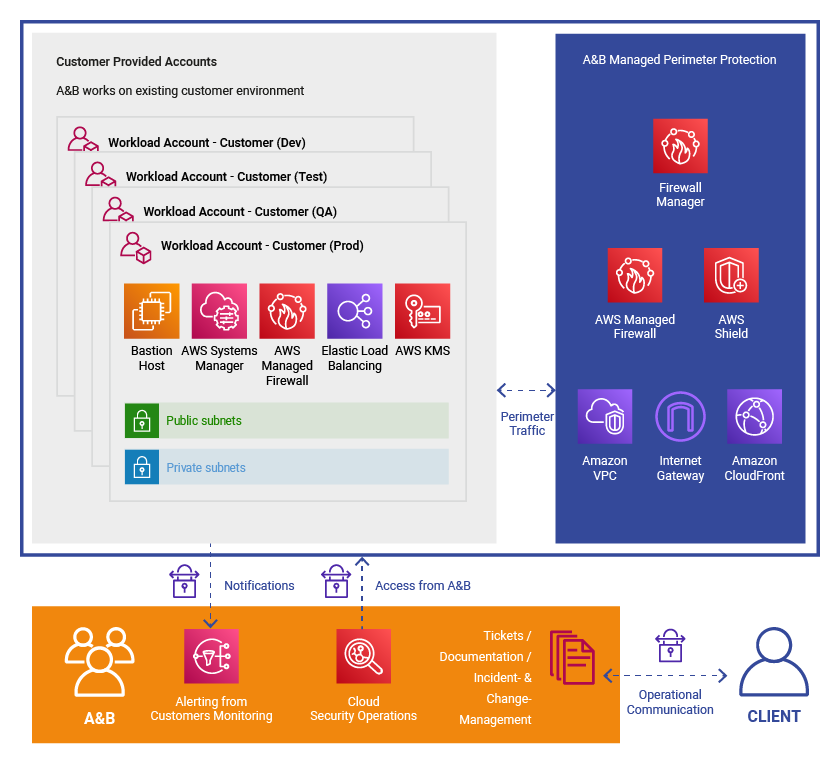
A&B Managed Perimeter Protection includes the following activities for customers:
- AWS account management
- Defining a security posture, including the applications, environments, and resources that are most critical to protect
- Full configuration of AWS Shield Advanced and AWS WAF
- Migration from other application security vendors
- Implementation of AWS Best Practices for DDoS Resiliency and Guidelines for Implementing AWS WAF
- Tuning of AWS Shield Advanced and AWS WAF to ensure optimal performance
- Monitoring resource health by testing architecture resiliency to avoid false negatives and false positives
- Building and maintaining customer specific runbooks
- First line support for all application security issues
- Escalation to the AWS DDoS Response Team (DRT) during events via Alice&Bob.Company support team
Optionally to the basic AWS WAF service, A&B provides third-party WAF solutions based on the market leading f5´s Advanced WAF and supports with extended f5 expertise.
how
Alice&Bob.Company connects existing AWS cloud infrastructure to Alice&Bob.Company’s Managed Perimeter Security environment. Therefore we maintain a dedicated AWS account for each client and routes the egress/ingress traffic through it.
According to customer´s requirements A&B implements one or more of the following services:
-
A&B activates WAF services and sets up a ruleset to secure customers applications on layer 7
Depending on customer requirements A&B will manage the rulesets according to an established workflow and setup subscriptions of rules to ensure up-to-date protection. - A&B enables AWS Shield (Standard or Advanced) and implements defensive workflows in close collaboration with the customer and the AWS DDoS Response Team
- A&B deploys and operates AWS Firewall Manager for a central & cross-account firewall management integrated in AWS Organizations
Alice&Bob.Company will start integration with a testing and tuning environment first. While assessing risks and implementing health monitoring, Alice&Bob.Company ensures optimal performance for real user traffic and avoids false positives.
Afterwards, the Managed Perimeter Protection is put into production. Therefore we
- place the AWS WAF into Allow/Block Mode,
- apply WAF to required resources with the AWS Firewall Manager and
- apply Shield Advanced to all required resources.
Alice&Bob.Company’s team of specialists will proactively handle events according to the proven incident management process, in order to minimize customer impact.
YOUR BENEFITS
Main advantages of using Managed Perimeter Protection with A&B:
- You take care on your product. We take care on the perimeter security of your applications. Continuously and managed.
- Gain DDoS protection and leverage protection from managed Web Application Firewalls
- Profit from our direct access to AWS DDoS-Mitigation-Team
other products in 04 continuous improvement
Continuous Penetration Testing
Minimize the risk of application vulnerabilities by combining manual and continuously automated penetration testing for your web applications and API’s.
Cloud Security Posture Management
Keeping visibility and enforced security across public cloud accounts – probably across multiple public cloud vendors with the right tools: facilitate a managed Cloud Security Posture Management (CSPM) service by Alice&Bob.Company.
Managed Container & Serverless Security
Have you heard about Kubernetes Security Posture Management (KSPM)? Keep a clear view on your Cloud and Serverless Security with A&B’s Managed Container & Serverless Security.
Security Chaos Engineering Program
Transfer the disruptive operational method of chaos engineering, developed initially by Netflix, to cloud security. We accompany your team(s) over the course of 12 month to establish the concepts and culture of Security Chaos Engineering (SCE).
CI/CD Pipeline improvement
Pimp your existing CI/CD pipeline to the next level! Alice&Bob.Company continuously monitors and improves your current CI/CD pipelines.
We continuously integrate automated and scalable Cloud Security into your software development lifecycle.
Security Champions Program
Cloud Security Trainings
Never stop learning! The cloud never stops teaching! In Jan 2021 AWS consists of more than 199 ready to use service. 45+ of those are security related. Let us help to enable and educate you team(s) with an individual training plan over a timeframe of 6 to 24 months.
Custom Tailored Managed Service
Is there anything you need, but we haven’t covered? We are always curious and eager to learn about your requirements. And maybe, we develop a new Cloud Security Managed Service together.