
Amazon Macie – Identify and protect customers private data
Personal or financial information is one of the most sought after goods for cyber criminals. Leaking such information can make a company’s customers vulnerable to

Personal or financial information is one of the most sought after goods for cyber criminals. Leaking such information can make a company’s customers vulnerable to

We are proud to announce that, we, the Alice&Bob.Company achieved the AWS Security Competency. We are one out of three companies holding this status in

There are numerous tools for Chaos Engineering such as Gremlin, the Chaos Automation Platform or Chaos Monkey. However, these SCE tools are of limited use

After introducing Security Chaos Engineering (SCE) as a potential approach to cloud security, we look at important differences between SCE and traditional security approaches. We

The first post discussed why traditional security concepts are insufficient for the cloud era. This post introduces Security Chaos Engineering (SCE) as an alternative approach

Distributed systems – especially cloud infrastructure – have become increasingly popular in recent years. However, cloud infrastructures have unique characteristics and therefore specific security demands.

We are super happy to be Gold Sponsor at this years AWS Summit in Berlin from 11th to 12th May 2022. The Summit brings the

Service Control Policies allow administrators central control over the maximum permissions of all accounts within their organization. We define, name strategies and look at the

Penetration Tests should be an important part of your company’s security strategy. Security experts – often external – try to find gaps in your IT
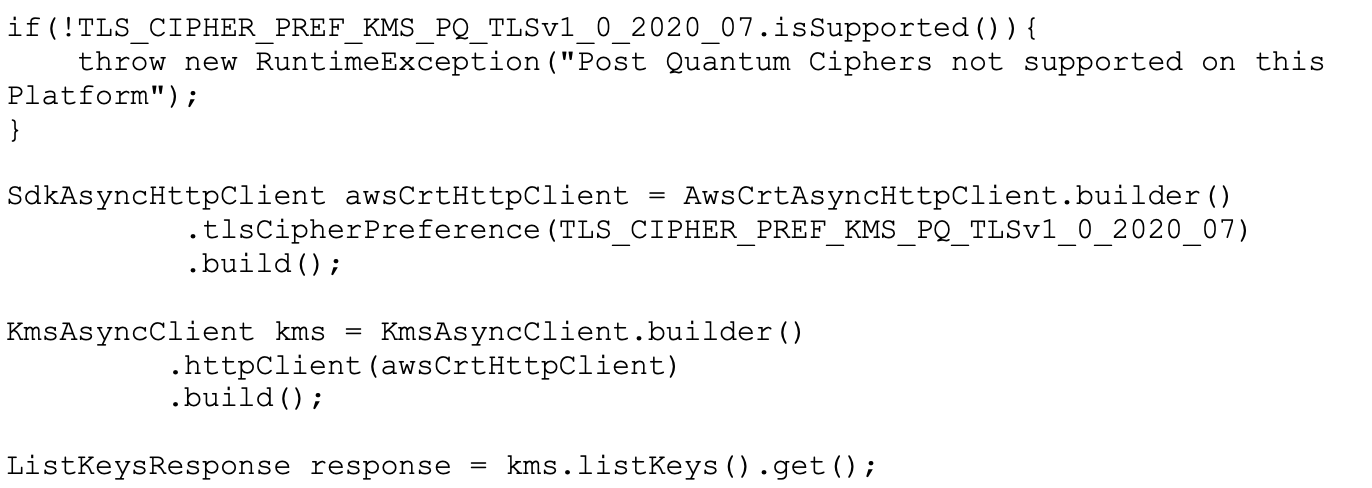
What happens to security with rise of quantum computers? How does AWS anticipate this revolution? In this article we’ll have a glimpse in to the