
Amazon Macie – Identify and protect customers private data
Personal or financial information is one of the most sought after goods for cyber criminals. Leaking such information can make a company’s customers vulnerable to

Personal or financial information is one of the most sought after goods for cyber criminals. Leaking such information can make a company’s customers vulnerable to

There are numerous tools for Chaos Engineering such as Gremlin, the Chaos Automation Platform or Chaos Monkey. However, these SCE tools are of limited use

After introducing Security Chaos Engineering (SCE) as a potential approach to cloud security, we look at important differences between SCE and traditional security approaches. We

The first post discussed why traditional security concepts are insufficient for the cloud era. This post introduces Security Chaos Engineering (SCE) as an alternative approach

Penetration Tests should be an important part of your company’s security strategy. Security experts – often external – try to find gaps in your IT
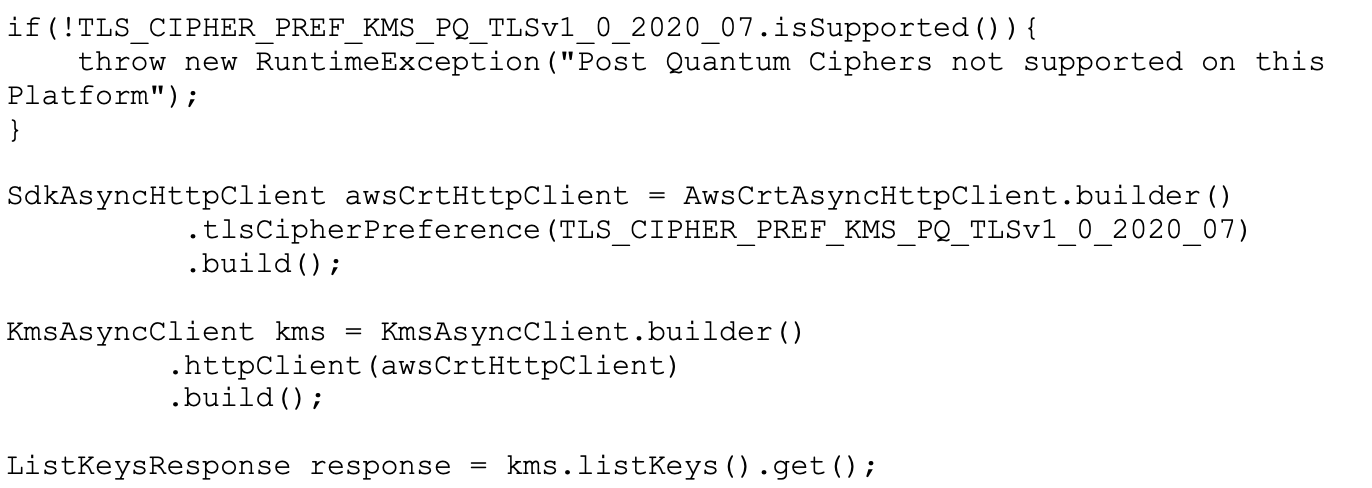
What happens to security with rise of quantum computers? How does AWS anticipate this revolution? In this article we’ll have a glimpse in to the

Welche Auswirkungen hat ein Quantencomputer auf die IT-Sicherheit? Wie antizipiert AWS diese Revolution? In diesem Artikel werfen wir einen Blick in die Zukunft und zeigen,

Update 15th Dec 2021: As the current situation is evolving security researchers noted that the presented quick fixes to mitigate the current log4j security vulnerability

Aqua Security offers a SaaS-platform for a number of security-related products for cloud environments. Together with the AWS-build-in-security-tools Aqua enables users to counter the numerous security risks associated with the configuration of AWS environments.

Complex AWS environment tend to have users or roles with more privileges granted than they really need. Finding those users and roles can be a time-consuming activity, so tool-support is needed for this task. CloudTracker is an Open-Source-tool for analyzing users, roles and their granted and used privileges.